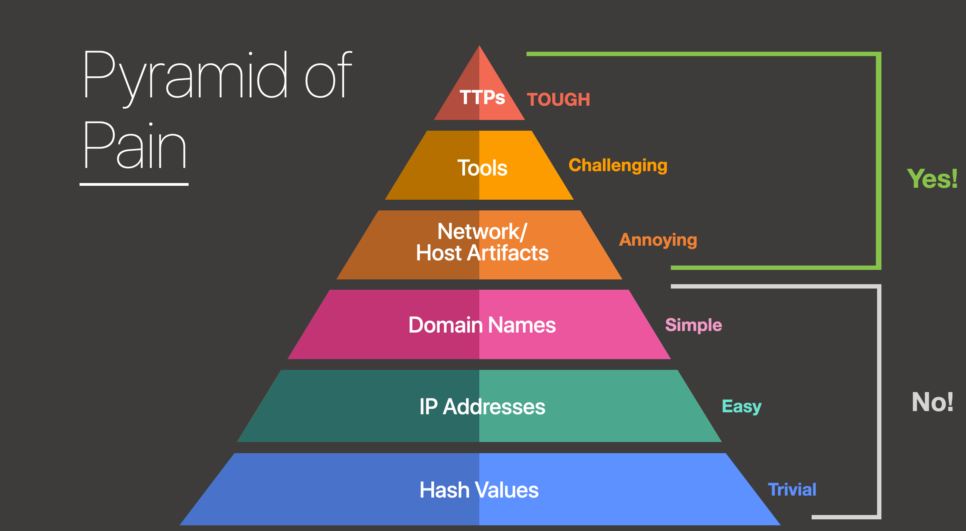
TShark Challenge I: Teamwork - EN

What is TShark and Why Use It?
TShark is the command-line version of Wireshark, one of the most widely used network protocol analyzers. While Wireshark offers a powerful graphical interface, TShark allows analysts to process packet capture (PCAP) files directly in the terminal — making it ideal for automation, scripting, and remote investigations.
For SOC analysts, TShark is especially valuable because it can be used to quickly extract indicators of compromise (IOCs), such as suspicious domains, IP addresses, and email strings, without needing to open a GUI. It supports filtering, field extraction, and integration with other tools in an investigation workflow.
Scenario
An alert was triggered:
“The threat research team discovered a suspicious domain that could pose a risk to the organization.”
As part of this simulated SOC challenge, my task was to analyze the provided teamwork.pcap file and extract key indicators of compromise.
Task 1: What is the full URL of the suspicious domain?
I navigated to the folder containing the PCAP file and ran the following command to extract unique HTTP host values:
tshark -r teamwork.pcap -T fields -e http.host | sort -r | uniq
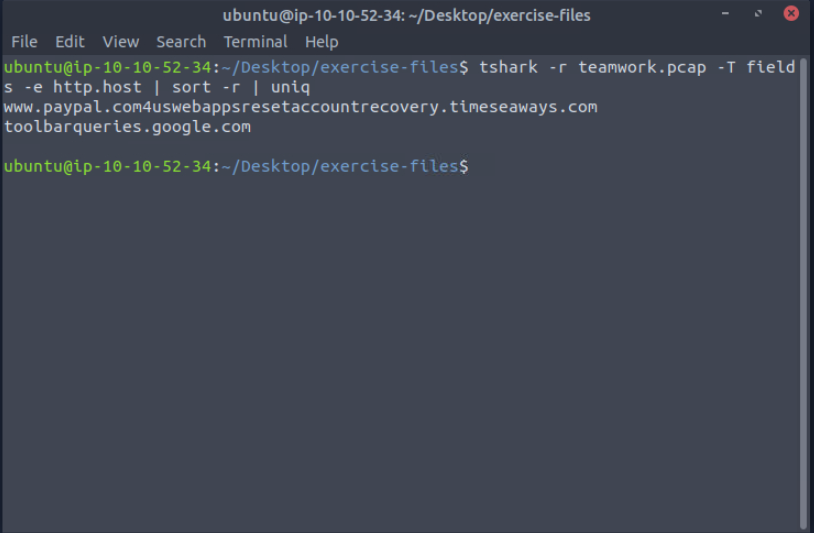
From the output, one domain stood out:
https://www.paypal.com4uswebappsresetaccountrecovery.timeseaways.com/
This domain mimics PayPal but includes suspicious elements, which is a common phishing tactic so I will have to put it in defang format to disable the link from incidental clicking.
hxxp[://]www[.]paypal[.]com4uswebappsresetaccountrecovery[.]timeseaways[.]com/
Task 2: When was the URL first submitted to VirusTotal?
I checked the suspicious domain on VirusTotal.
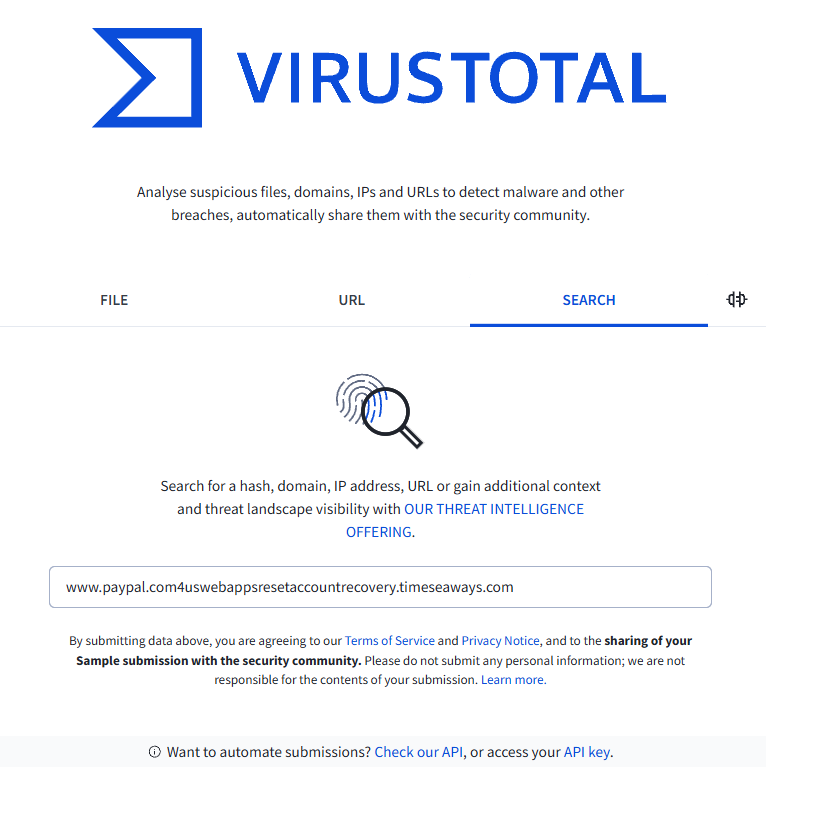
Once the search results load, I proceed to the details section.
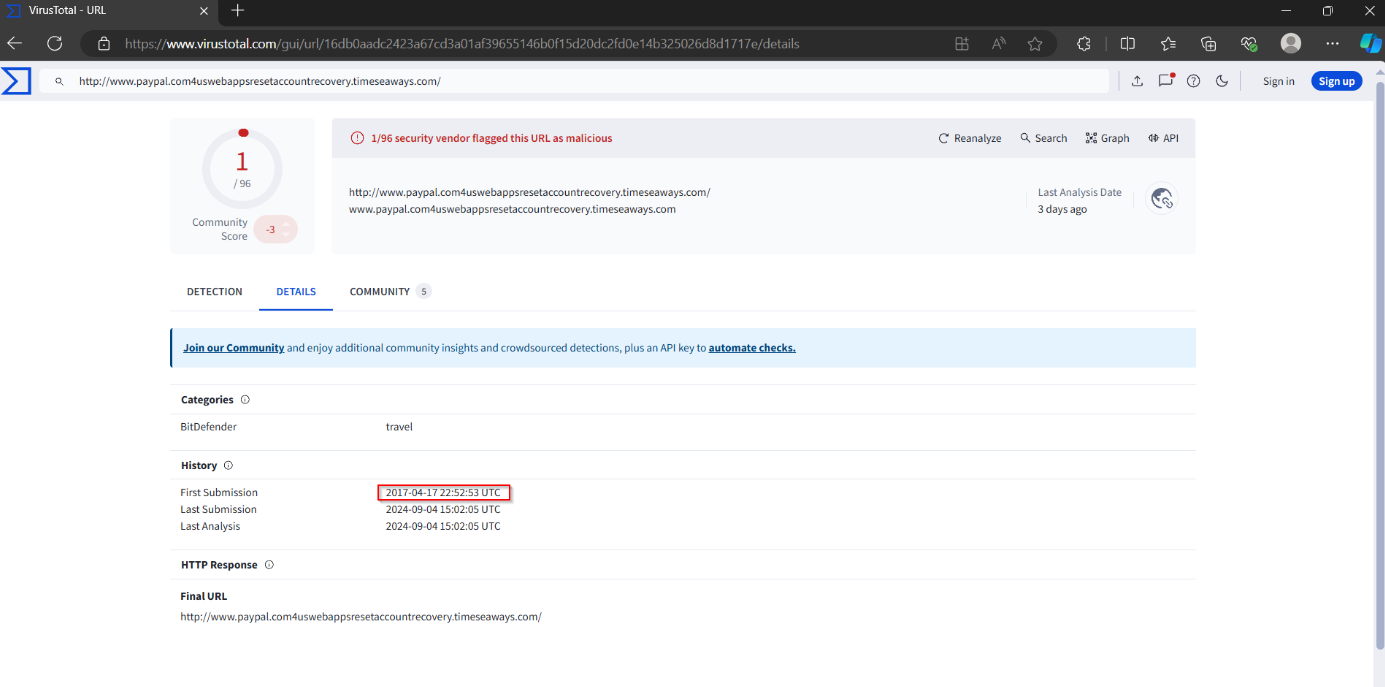
In the “Details” section of the report, the first submission date was: 2017-04-17 22:52:53 UTC
Task 3: Which known service was the domain trying to impersonate?
From the domain name structure (using “paypal.com” as part of a subdomain), it is clearly impersonating: PayPal
Task 4: What is the IP address of the malicious domain?
To extract DNS information from the PCAP, I ran:
tshark -r teamwork.pcap -T fields -e dns.qry.name -e dns.a | sort -u
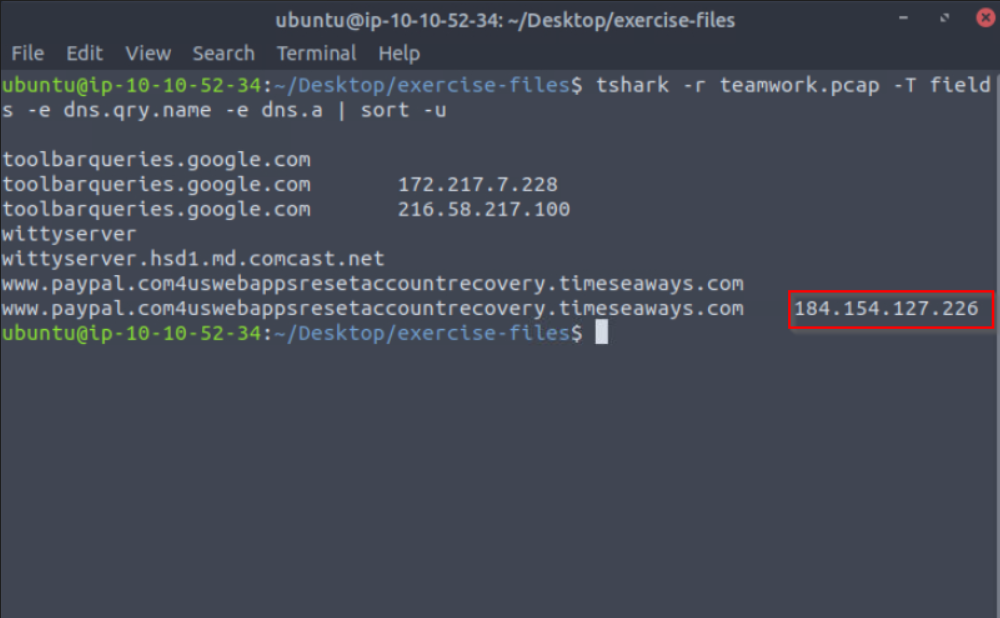
From the output, the IP address linked to the phishing domain is: 184[.]154[.]127[.]226 in defang format to prevent unintentional clicking
Task 5: What email address was used?
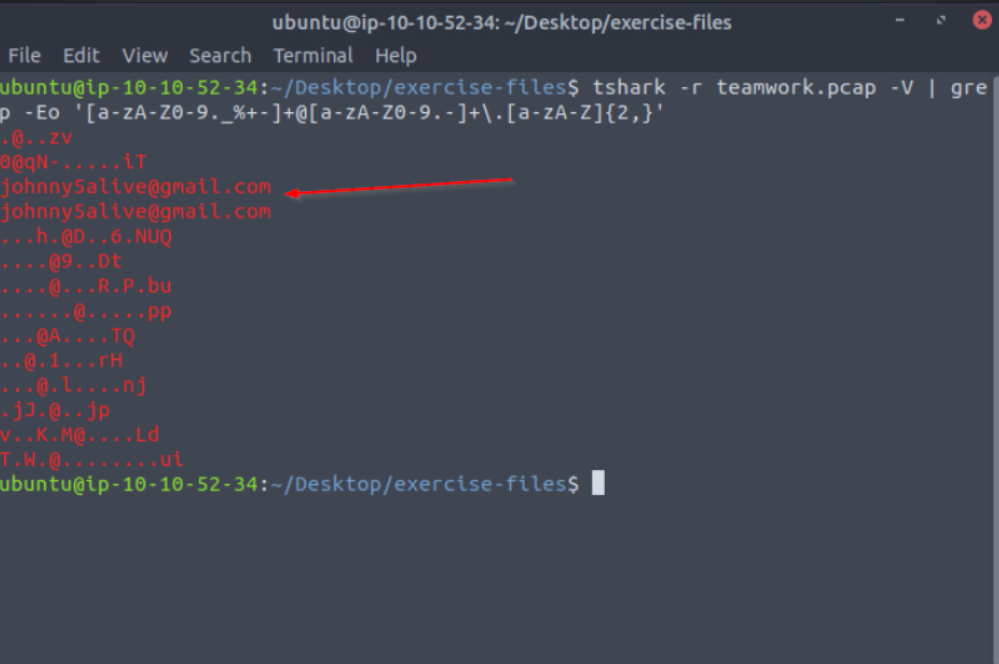
To check whether any email addresses were transmitted in the captured traffic, I used the following command:
tshark -r teamwork.pcap -V | grep -E "\w+@\w+\.\w+"
Explanation of the Command:
- tshark: The command-line version of Wireshark, used for packet capture and analysis.
- -r teamwork.pcap: Tells TShark to read from the file teamwork.pcap.
- -V: Enables verbose output, displaying full packet details for each captured packet.
- |: The pipe symbol passes the output of the TShark command to the next command.
- grep -E: Enables extended regular expressions (regex), which allows for more complex pattern matching.
- "\w+@\w+\.\w+": This regex pattern looks for strings that resemble basic email addresses:
- \w+ matches one or more alphanumeric characters (letters, digits, or underscore).
- @ matches the “at” symbol.
- \w+ again matches the domain name part.
- \. matches the dot before the domain suffix (like .com).
- \w+ matches the final part of the domain (e.g., "com", "net", etc.)
This pattern isn’t perfect for all email formats, but it’s effective for catching basic ones in raw packet data.
From the output, the email address that appeared in the capture was: johnny5alive[at]gmail[.]com
Note: The email is intentionally obfuscated (e.g., replacing @ with [at]) to avoid spam scraping and emphasize that it’s a suspicious or malicious address.
This challenge helped me understand:
How phishing domains are designed to deceive users
How to use TShark to extract key indicators from network traffic
How DNS, HTTP, and metadata can reveal the footprint of an attack
Powered by Froala Editor
Comments (0)
No comments yet. Be the first to comment!